Raspberry Pi SSH tunnel has become a crucial tool for developers, hobbyists, and professionals alike who are looking to secure their remote connections and data transmissions. Whether you're setting up a home server, accessing your Raspberry Pi remotely, or securing sensitive information, understanding how to use SSH tunnels effectively is essential. This guide will delve into the nuances of Raspberry Pi SSH tunnel, providing step-by-step instructions and valuable insights.
Raspberry Pi SSH tunnel is a powerful feature that allows users to create encrypted communication channels between devices. With the growing demand for secure remote access and privacy protection, mastering this technique is more important than ever. Whether you're a beginner or an advanced user, this article will provide you with the knowledge and tools necessary to implement SSH tunnels securely and efficiently.
In this comprehensive guide, we will explore the fundamental concepts of SSH tunnels, step-by-step setup instructions, troubleshooting tips, and advanced configurations. By the end of this article, you will have a thorough understanding of how Raspberry Pi SSH tunnel works and how to leverage it for your specific needs. Let's dive in!
Read also:Where Is The Zac Brown Band From Exploring The Roots And Journey Of This Iconic Band
Table of Contents:
- Introduction to SSH Tunnel
- Raspberry Pi Basics
- Why Use SSH Tunnel?
- Setting Up SSH on Raspberry Pi
- Creating an SSH Tunnel
- Advanced SSH Tunnel Configurations
- Troubleshooting SSH Tunnel
- Security Best Practices
- Use Cases for SSH Tunnel
- Conclusion and Next Steps
Introduction to SSH Tunnel
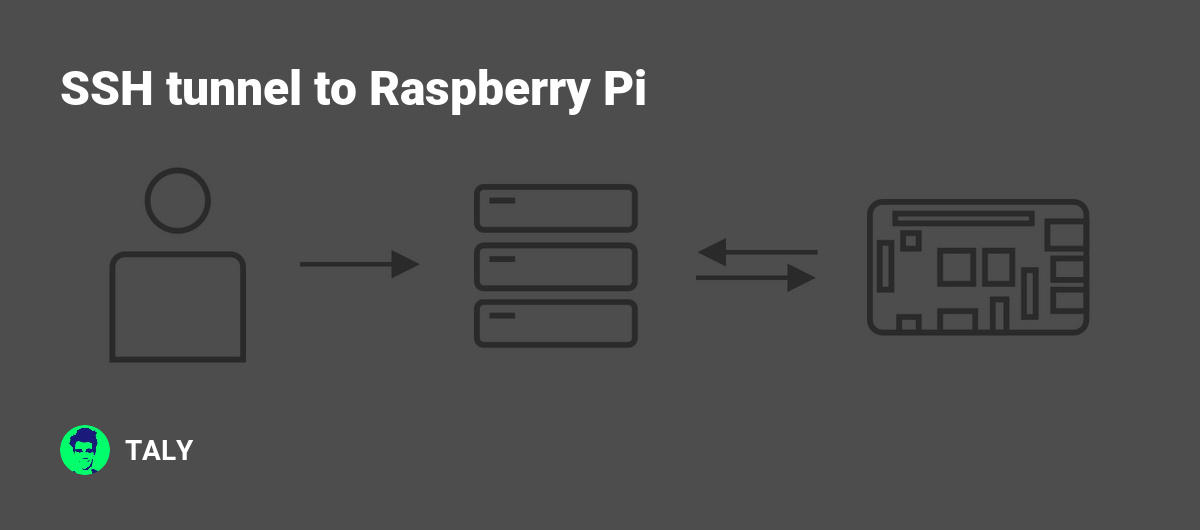
SSH (Secure Shell) is a cryptographic network protocol that enables secure communication between two devices over an unsecured network. An SSH tunnel, also known as port forwarding, allows you to securely transfer data between devices by encapsulating it within an encrypted SSH connection. This technique is particularly useful when accessing sensitive information or managing remote servers.
One of the most popular platforms for experimenting with SSH tunnels is the Raspberry Pi. Due to its affordability, versatility, and ease of use, the Raspberry Pi has become a favorite among tech enthusiasts for setting up home servers, IoT devices, and secure communication channels. Understanding how to set up an SSH tunnel on Raspberry Pi can significantly enhance your ability to manage and secure your network.
Raspberry Pi Basics
What is Raspberry Pi?
Raspberry Pi is a series of small single-board computers developed by the Raspberry Pi Foundation. Designed primarily for educational purposes, the Raspberry Pi has evolved into a versatile platform used in various applications, from home automation to industrial projects. Its compact size, low power consumption, and affordability make it an ideal choice for developers and hobbyists.
Key Features of Raspberry Pi
- Compact and lightweight design
- Support for multiple operating systems, including Linux-based distributions
- GPIO (General Purpose Input/Output) pins for interfacing with external devices
- Wi-Fi and Ethernet connectivity options
- Extensive community support and documentation
These features make the Raspberry Pi an excellent platform for experimenting with SSH tunnels and other networking technologies.
Why Use SSH Tunnel?
SSH tunnels offer several advantages over traditional unsecured connections:
Read also:Buscar Kid And His Mom Cctv Video Original A Deep Dive Into The Viral Sensation
- Encryption: SSH tunnels encrypt all data transmitted between devices, ensuring privacy and security.
- Remote Access: You can securely access your Raspberry Pi or other devices from anywhere in the world.
- Bypassing Firewalls: SSH tunnels can help bypass restrictive firewalls and network policies.
- Data Integrity: SSH ensures that data transmitted over the network remains intact and unaltered.
For users concerned about privacy and security, SSH tunnels provide a robust solution for safeguarding sensitive information.
Setting Up SSH on Raspberry Pi
Enabling SSH on Raspberry Pi
Before creating an SSH tunnel, you need to enable SSH on your Raspberry Pi. Follow these steps:
- Power off your Raspberry Pi and insert the microSD card into your computer.
- Create an empty file named "ssh" (without any file extension) in the boot partition of the microSD card.
- Insert the microSD card back into your Raspberry Pi and power it on. SSH will now be enabled.
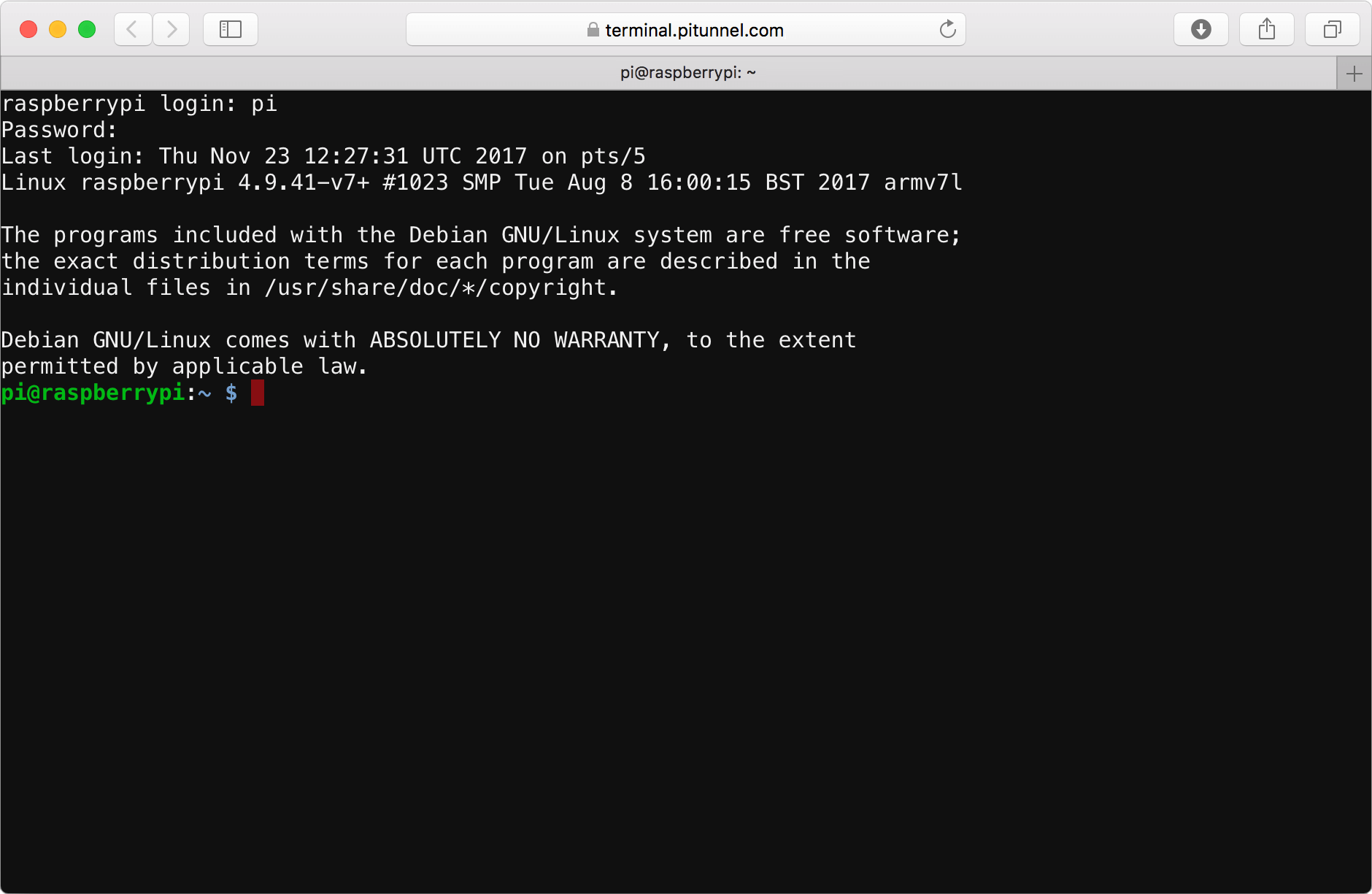
Connecting to Raspberry Pi via SSH
To connect to your Raspberry Pi via SSH, you will need the IP address of your device. You can find this information using the following methods:
- Check your router's connected devices list.
- Use the "ifconfig" or "ip addr" command on the Raspberry Pi terminal.
Once you have the IP address, use an SSH client like PuTTY (Windows) or Terminal (Mac/Linux) to establish a connection:
ssh pi@Enter the default password ("raspberry") when prompted, or use your custom password if you have changed it.
Creating an SSH Tunnel
Basic SSH Tunnel Configuration
Creating an SSH tunnel involves forwarding a local port to a remote server. Use the following command to set up a basic SSH tunnel:
ssh -L ::@ For example, to forward traffic from your local machine's port 8080 to a remote server's port 80, use:
ssh -L 8080:www.example.com:80 pi@Dynamic SSH Tunnel (SOCKS Proxy)
A dynamic SSH tunnel acts as a SOCKS proxy, allowing you to route all traffic through the SSH connection. This is particularly useful for web browsing or accessing blocked websites:
ssh -D @ Configure your web browser to use the SOCKS proxy with the specified local port for secure browsing.
Advanced SSH Tunnel Configurations
Reverse SSH Tunnel
A reverse SSH tunnel allows you to access a device behind a firewall or NAT from the outside. Use the following command to set up a reverse tunnel:
ssh -R :localhost:@ This configuration is useful for remotely accessing your Raspberry Pi when it is located behind a restrictive network.
Persistent SSH Tunnel
To ensure your SSH tunnel remains active even after network interruptions, use tools like autossh or systemd services. Autossh automatically restarts the SSH connection if it drops:
autossh -M 0 -N -L ::@ This setup ensures continuous connectivity and reliability.
Troubleshooting SSH Tunnel
Common issues when setting up an SSH tunnel include connection timeouts, incorrect port configurations, and firewall restrictions. Here are some troubleshooting tips:
- Verify the IP address and port numbers used in the SSH command.
- Check your router's port forwarding settings if you're accessing the Raspberry Pi from outside your local network.
- Ensure that the SSH service is running on the Raspberry Pi and that the firewall allows incoming SSH connections.
Refer to the official Raspberry Pi documentation or community forums for additional support.
Security Best Practices
While SSH tunnels enhance security, it's essential to follow best practices to protect your data:
- Use strong, unique passwords or public key authentication for SSH access.
- Limit SSH access to trusted IP addresses using firewall rules.
- Keep your Raspberry Pi's operating system and SSH server software up to date with the latest security patches.
Implementing these measures will help safeguard your Raspberry Pi and prevent unauthorized access.
Use Cases for SSH Tunnel
SSH tunnels have a wide range of applications, including:
- Secure remote access to Raspberry Pi or other servers.
- Encrypted file transfers using SCP or SFTP.
- Bypassing geo-restrictions for accessing blocked websites.
- Protecting sensitive communications in public networks.
By leveraging SSH tunnels, you can enhance the security and functionality of your Raspberry Pi projects.
Conclusion and Next Steps
Raspberry Pi SSH tunnel is a powerful tool for securing remote connections and protecting sensitive data. By following the steps outlined in this guide, you can set up and configure SSH tunnels effectively, unlocking the full potential of your Raspberry Pi. Remember to adhere to security best practices and continuously update your knowledge to stay ahead of emerging threats.
We invite you to share your thoughts and experiences in the comments section below. Feel free to explore our other articles for more insights into Raspberry Pi and networking technologies. Together, let's build a safer and more connected digital world!
Sources: